British reconstructed bombe
|
The battle of wits between codemakers and codebreakers has been the driving force for innovation in cipher technology for many centuries.
Every time the codemakers invented the next advancement in cipher technology, the codebreakers would find an ingenious way to break
that cipher. This website explores the technology of these crypto devices and the dramatic consequences of codebreaking to history.
The science and history of cryptology is shrouded in secrecy and confusion. As the veil is lifted on these secrets, often many decades
or centuries after the fact, we gain a greater understanding of how codebreaking changed the traditional view of history. As a result,
we are forced to re-examine and rewrite that history. Also, the invention and inventors of many cipher technologies are kept secret for
many years. Examples of cipher technologies traditionally credited to the wrong inventors include: the Enigma machine, the Vigenère disk,
the one-time pad, the Jefferson wheel cypher, the Wheatstone cipher and even modern public key encryption!
The battle for cipher supremacy is intertwined with advances in closely aligned technologies such as; radio, telephone, teletype,
computers and the internet. Sometimes, a new technology will be the catalyst for a new cipher machine and sometimes it will be the
catalyst for codebreaking. The invention of the vacuum tube played both roles. Because of the widespread use of the new invention of
radio in WW1, for example, every country was surprised to find that their ciphers were broken. This spurred the next phase of crypto
development, which was then broken in WW2 by the codebreakers’ use of vacuum tubes, which were used in the world’s first computers.

Jefferson Wheel Cypher
|
As an example of history being rewritten, the knowledge of the Allies breaking the Nazi Enigma code in WW2 was kept secret for 29 years,
despite over 15,000 people working to break that code. In today’s world of WikiLeaks, Edward Snowden and the internet, it is hard to fathom
how this bombshell story was kept secret for so long. Now the impact of the Allies breaking the Enigma code is better understood. By some
estimates, it shortened the war by two years, saving millions of lives.
An example of delayed revelation in WW2 was the Nazi General Rommel’s codebreaking of Allied messages during the Africa campaign. His
moniker of “Desert Fox” may need to be reconsidered, or maybe his foxy tactics can now be correctly attributed to code breaking instead
of military cunning. Rommel’s tactics and the Nazi invasion of Africa ultimately failed, however, after the Allies gained the upper hand
in the escalating crypto wars.
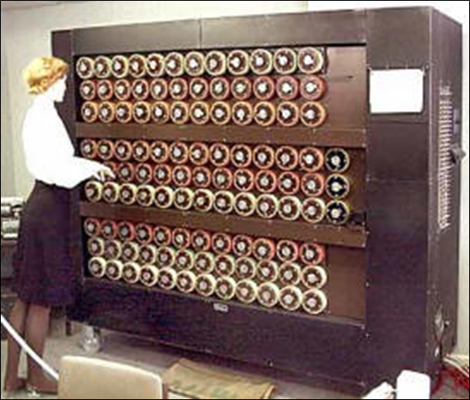
Another important historical impact of breaking the German codes was the invention of electronic computing. The British bombe was a special
purpose computing machine used to break the Enigma code and the US version added the innovation of digital memory, using electron tubes.
The British Colossus used 2400 electron tubes and was designed to break the German teletype cipher, not the Enigma machine as is sometimes
erroneously reported. It is now recognized as the world’s first electronic, digital and programmable computer.
In the Pacific theater in WW2, the turning point in the war was the Battle of Midway, where the Japanese plan for a surprise attack was
deciphered and thwarted by the US decryption of their Purple and naval codes. Also, Admiral Yamamoto, the mastermind of the attack on Pearl
Harbor, was assassinated based on decrypted Japanese messages.

Hebern electro-mechanical rotor machine
|
It was originally thought the electric rotor ciphers were invented independently by 4 inventors in 4 countries at the end of WW1. It wasn’t
until 2003 that it was discovered this pivotal innovation was actually invented several years earlier, in 1915, by two Dutch naval officers.
In addition, 2 of the 4 inventors were not independent at all, but collaborated after stealing the information from the two Dutch inventors.
The previously credited inventor of the Enigma machine, the German engineer Arthur Scherbius, was one of the two inventors who stole the Enigma
machine design. Now history has been rewritten on the invention of the most infamous cipher machine of them all, with credit going to the Dutch
naval officers, Theo van Hengel and Rudolf Spengler.
The only cipher that is mathematically proven to be completely unbreakable is the one-time pad. Even this perfect cipher has been broken,
however, when not used correctly. This misuse caused historic consequences during WW2 for Germany and the cold war for the Soviet Union.
The Germans used an algorithm to generate random numbers, which means the numbers were not truly random, so these one-time pad messages were
decoded by the Allies for decades. The Soviets re-used some one-time pads, making them 2 or 3-time pads. This crypto sloppiness was exploited
by the US in the Venona Project, which identified 349 Soviet spies in the US and UK. Once again, this cipher technology was credited to the
wrong inventors for almost 100 years. It was thought to be invented by Gilbert Vernam and Joseph Mauborgne in 1919 but a 2011 discovery proved
it was invented and published in a code book by a Sacramento banker, Frank Miller, 37 years earlier in 1882.
When cryptanalysis fails, espionage is the favored and logical next step in the battle of wits. It was espionage that gave the Polish their
first break in decrypting the German Enigma machine. The US National Security Agency “back-door” into the Hagelin cipher gave the US an open
book into the military, diplomatic and government secrets of over 100 countries for four decades. This represents one of the greatest stings
in history!
The NSA “assistance” in developing Data Encryption Standard (DES) in the 1970s resulted in a curious and unnecessary reduction of the key
size from 64 to 56 bits. DES continued to use 64 bits in its algorithm, but 8 of those bits were simply unused. It was speculated the key
size reduction allowed the NSA to break DES by brute force in the 1970s. In a public demonstration in 1999, DES was broken by a brute force
attack of networked PCs in 22 hours, confirming those earlier suspicions of NSA’s capabilities and intentions.

Official NSA PR photo, the agency gets a message from above
|
The NSA was concerned about the increasing strength of publicly available voice encryption and developed their ill-fated “Clipper chip” in
1993 to give the US government a publicized back door into all communications. It was only because of a design flaw in the Clipper chip that
this backdoor was not required to be installed in all US communication products. The codemakers exploited this Clipper chip failure by quickly
disseminating an open source software encryption program called Pretty Good Privacy, or PGP, which is still in use today. Not to be outdone,
the NSA resorted to secret agreements with major hardware and software firms to allow them backdoor access into much of the voice and electronic
communications traversing the internet.
Recent news of wholesale gathering of phone metadata by the NSA on hundreds of millions of people captivated and appalled people worldwide,
but even more consequential is the fact they broke into public key encryption. Some of the backdoors and secret agreements have now been
disclosed and some companies have been paid millions of dollars to help the NSA engineer these backdoors into their products. The existence
of a backdoor in any product means that product has a built-in weakness, since a backdoor is still a door which can be exploited by nefarious
codebreakers. The NSA may not even be dependent on these back doors any more, since it has been reported they have broken into many public key
encryption systems.
The battle of wits between codemakers and codebreakers continues to escalate and is guaranteed to produce more ingenious technologies and
interesting revision of history for years to come.